Provide technical knowledge and support for Windows 7,Windows 8,windows 10, Windows server 2008,Windows Server 2012, Speed up Computer, Virus and malware remmoval, Operating System Installation and Repairing, Cisco Router, Cisco Switches and Cisco ASA
Wednesday, 30 September 2015
Tuesday, 29 September 2015
How to check router command history
Router Command History:-
Command
|
Result
|
Ctrl+P or Up arrow
|
Shows last command
|
Ctrl+N or Down arrow
|
Shows previous commands entered
|
show history
|
Shows last commands
|
show terminal
|
Shows terminal configurations and history buffer size
|
terminal history size
|
Changes buffer size (max 256)
|
Ex. Show history:-
Ex. Show terminal command
Change history buffer size :-
How to connect Cisco router and configure clock
Connecting to Router :-We can connect Cisco router using Telnet, SSH, Console Cable and ASDM. ASDM provide GUI console, But command line interface is the best way to configure a Cisco router.
Logging to Router :-After router boot process complete Press Enter. Router will prompt router>. This is User Exec Mode.
This mode is used to view the settings of router.
To change the router configuration you have to switch to Privilege Exec and Global Configuration mode.
To enter in Privilege Exec Mode type:- enable and press enter
Ex. Router > enable
Router #
To exit from privilege mode :-
Router # logout
Or
Router # disable
Global Configuration Mode :- Change we make in this mode will affect the entire router.
To enter in global configuration mode:-
If you make any change here, it will save in running config file or RAM. To save changes in startup config or NVRAM enter the following command
Copy runnig-config startup-config
How to configure cisco router interfaces:- To configure interface use interface command in global configuration mode
Router(config)# interface ?
Ex:-
Choose interface which you wants to configure, I am going to configure FastEthernet.
R1(config)#interface fastEthernet 0/0
R1(config-if)#
Notice that the prompt changed to Router(config-if)#? This tells you that you’re in interface configuration mode. And wouldn’t it be nice if the prompt also gave you an indication
of what interface you were configuring?
Available commands in mode :-You can use ? to check available commands in any mode
Set Clock in router:-
R1#clock set
R1#clock set ?
hh:mm:ss Current Time
R1#clock set 11:46:50 ?
<1-31> Day of the month
MONTH Month of the year
R1#clock set 11:46:50 29 september ?
<1993-2035> Year
R1#clock set 11:46:50 29 september 2015?
<1993-2035>
R1#clock set 11:46:50 29 september 2015
R1#
*Sep 29 11:46:50.000: %SYS-6-CLOCKUPDATE: System clock has been updated from 01:22:08 UTC Fri Mar 1 2002 to 11:46:50 UTC Tue Sep 29 2015, configured from console by console
Friday, 25 September 2015
Internet Protocols
User Datagram Protocol (UDP):- UDP is a connectionless transport layer protocol.
The term connectionless means it does not create virtual circuit before start transfer
data or it does not send SYN and Ack packets. UDP does not sequence the segments and does not care in which order the
segments arrive at the destination. Because of this, it’s referred to as an unreliable protocol.UDP is
very fast than TCP but not reliable. So where we need speed to transfer data we
use UDP Ex. VOIP, for reliable communication we use TCP.
Port Numbers:- All
protocols have a predefined port number on which they receive data or packets.
To send data there must be both port number for source and destination, Source
port assign randomly or dynamically but destination port number always be well
known. Ports from 0 to 1023 are well known ports.
Internet Layer Protocol
- IP
- ARP
- ICMP
- Proxy ARP
IP :- IP receives
segments from the Host-to-Host layer and fragments them into datagram’s if necessary. IP then reassembles datagram’s
back into segments on the receiving side. Each datagram is assigned the IP
address of the sender and of the recipient. Each router that receives a
datagram makes routing decisions based on the packet’s destination IP address.
TTL:- The time to
live is set into a packet when it is
originally generated. If it doesn’t get
to where it wants to go before the TTL expires, This stops IP
packets from looking for a destination .
Protocol:- Port of upper-layer protocol. Also supports Network layer
protocols.
Header checksum:
- Cyclic redundancy check (CRC) on header only.
Source IP Address:
- 32-bit
IP address of Source Device.
Destination
IP address: - 32-bit
IP address of the destination device.
IP options:- Used for
network testing, debugging, security.
Data:-
After
the IP option field will be the upper-layer data.
ARP:- Address
Resolution Protocol is used to resolve MAC address from IP address. If IP doesn’t
find the destination host’s hardware address in the ARP cache, it uses ARP to
find MAC.
ICMP:- Internet
control messaging protocol is a management and messaging protocol for IP.
Proxy ARP:- Proxy ARP
can actually help machines on a subnet reach remote subnets without configuring
routing or even a default gateway. Proxy Using ARP will definitely increase the
amount of traffic on your network segment, and hosts will have a larger ARP
table than usual in order to handle all the IP-to-MAC address mappings
Thursday, 17 September 2015
Internet protocol
Network Protocols
The DOD model is a Brief version of the OSI model, it has four layers.
1. Application layer
2. Host to Host Layer
3. Internet Layer
4. Network Access layer
DOD and OSI Layers
TCP/IP Model Protocols
Application Layer Protocols
Telnet:- It is a protocol that allows a user to access Telnet server or machine remotely through command line.
TFTP:- TFTP (Trivial File Transfer Protocol) is used to transfer file over the network. It does not provide the directory browsing feature. So to use this protocol we must know the exact file name and location of file.
FTP:- FTP(File Transfer Protocol) is actual file transfer protocols. We can transfer data or file using the FTP protocol. FTP is not just a protocol, It is a program also that provide directory browsing feature and let users select data what they need to transfer.
SMTP:- SMTP(Simple Mail Transfer Protocol) is used to send E-mail messages. It is responsible for successful message delivery. It continuously check queue for messages, as message comes in queue it process that message to deliver.
LPD:- (Line Printer Daemon) is designed for printer sharing. It allows to send print command over the network.
X Window:- X Window defines a protocol for writing client/server applications
based on a graphical user interface (GUI). The idea is to allow a program, called a client,
to run on one computer and have it display things through a window server on another computer
SNMP:- (Simple Network Management Protocol) is used to collect information about network. It is also called watchdog over the network. When any problem occur in network SNMP send alert to the management machine.
NFS:- NFS(Network File System) is used for file sharing. It allows to different file systems to share data.
Transmission Control Protocol
TCP:- TCP(Transmission Control Protocol) take data payload from upper layers and break them into segments.TCP is a connection oriented protocol , it means tit create a virtual circuit before transfer data segments. It is also called hand shaking. During this initial handshake, the two TCP layers also agree on the amount of information that’s going to be sent before the recipient’s TCP sends back an acknowledgement. With everything agreed upon in advance, the path is paved for reliable communication to take place.
Destination port :- The port number of the application requested on the destination host.
Sequence number :- Puts the data back in the correct order or retransmits missing or damaged
data, a process called sequencing.
Acknowledgement number:- Defines which TCP octet is expected next.
Header length:- The number of 32-bit words in the TCP header. This indicates where the data
begins. The TCP header (even one including options) is an integral number of 32 bits in length.
Reserved:- Always set to zero.
Code bits :- Control functions used to set up and terminate a session.
Window :- The window size the sender is willing to accept, in octets.
Checksum :- The cyclic redundancy check (CRC), because TCP doesn’t trust the lower layers
and checks everything. The CRC checks the header and data fields.
Urgent :- A valid field only if the Urgent pointer in the code bits is set. If so, this value indicates
the offset from the current sequence number, in octets, where the first segment of non-urgent
data begins.
Options:- May be 0 or a multiple of 32 bits, if any. What this means is that no options have to be
present (option size of 0). However, if any options are used that do not cause the option field to total
a multiple of 32 bits, padding of 0s must be used to make sure the data begins on a 32-bit boundary.
Data :- Handed down to the TCP protocol at the Transport layer, which includes the upper layer
headers.
Monday, 14 September 2015
Windows Server Introduction
About Windows Server 2008
Microsoft released multiple edition of "Windows Server 2008" .
You can purchase these edition for both 32 bit and 64 bit. In Server 2008 Microsoft introduced some new features, Hyper-V is one of them.
Hyper-V :- Hyper-V is a virtualization technology, in which we can run multiple operating system concurrently on the same system. Using Hyper a single server can act like multiple servers.
Hyper-V is only available for 64 bit operating systems.
Windows Server 2008 Editions
1.Windows Server 2008 Standard Edition :- This edition is for small and medium size organizations.
This is available for both, with and without Hyper-V.
With Hyper-V it support only one virtual server.
2. Windows Server 2008 Enterprise Edition :- This edition is for large organizations. This is available with and without Hyper-V. With Hyper-V it support up to four virtual servers. Enterprise edition also support clustering and hot swappable memory.
3. Windows Server 2008 Datacenter :- Datacenter edition is used for high end applications and large scale virtualization. This edition provides all features of enterprise edition with unlimited virtual server and hot swappable memory and processor feature.
4. Windows Server 2008 Web Edition :- This edition is designed on for web hosting.
New Security Features in Windows Server 2008
1.Bit Locker :- Bit locker is new feature introduced in server operating system. Bitlocker encrypt entire data volume and make it difficult to boot with another added volume.
2. NAP (Network Access Protection):- NAP protect our server from unhealthy or virus infected remote users.
3. Server Manager :- Server manager is a new console in which you can mange entire server roles and feature from single location.
4. Sever Core :- Server core allow to you only install required application to support for specific role.
Server core does not have GUI interface, It only have command line user interface.
5. Power Shell :- Power shell is a strong command line management tool. It allow you to combine commands and shell scripting.
You can use power shell with :
a). Exchange server
b). IIS
c). Active directory Domain services
d). Terminal server
e). Registory management
6. Read Only Domain Controller :- RODC host a read only copy of active directory database.
How To Install Windows Server 2008
1. Insert Windows Server 2008 DVD and restart computer
2. Press any key when system prompt "Press any key to boot from CD or DVD
3. Select language and click "Next"
4. Click "Install Now"
5. Select operating system Edition and click next
6. Accept the License Terms and click next
7. Click on custom
8. Select disk partition and click next
9. Installation Process Will Start..
10. Once installation process will complete, It will prompt for password change
11.Click OK to change password
12. Enter new password and enjoy.
Active Directory
Active Directory is a database that contains information about available resources in a domain forest. It allows client to find objects within a namespace. Anything that a active directory contain is considered as a object. An object can be any user, system, printer or any resource within Active Directory.
Domain Introduction
Domain is a logical group of object such as Users, computer, resources that share the same Active Directory database.
Domain Classification
1. Root Domain :- The Root domain is very first domain created in Active Directory forest. For example "Google.com" is a root domain
2. Child Domain :- Child domain shares the namespace of root domain. For example "translate.google.com" , "Maps.google.com".
3. Tree :- Tree is a group of domains that share the same namespace.
4. Forest:- Forest is the highest level of Active directory. Forest contain domain tree.
Thursday, 10 September 2015
How to enable advance password security for Windows 7
1. Go to Run and type "syskey" and click ok
2. Click yes
3. Click "update"
4. Enter password and click ok
5.click ok
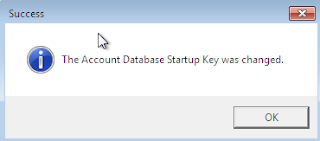
6. Restart computer, now windows will not boot until you will not enter correct password.
These steps will encrypt SAM Database (Security Account Manager) and it is very difficult to bypass or break this.
1. Go to Run and type "syskey" and click ok
2. Click yes
3. Click "update"
4. Enter password and click ok
5.click ok

6. Restart computer, now windows will not boot until you will not enter correct password.
These steps will encrypt SAM Database (Security Account Manager) and it is very difficult to bypass or break this.
Subscribe to:
Comments (Atom)


























